Rate this article :
5/5 | 2 opinion
This article was useful to you ?
Yes
No
Vous avez noté 0 étoile(s)
Sommaire
Procédure
Around 30% of Internet websites use WordPress, making it the most popular CMS in the world. Unfortunately, the incredible popularity of WordPress has one major drawback: it makes the platform very attractive to hackers.
A common attack vector used against WordPress websites involves compromising files so that the website automatically redirects users to another location. In this tutorial you will learn how to remove this redirection.
There are many types of malicious redirection techniques used on WordPress websites. The most common include:
Every WordPress website has an .htaccess file located in the folder where WordPress was installed. WordPress uses this file to change the way the web server handles files. It is also used to create the pretty permalinks used by WordPress. Hackers accessing your server can modify this file to add an illegal redirect. The redirect would send all visitors to another website.
Hackers could also add additional .htaccess files containing an illegal redirect to other locations, such as / wp-content or / wp-includes.
2. Modifying WordPress PHP files
WordPress often contains malicious redirects in PHP files, including index.php, header.php, footer.php and functions.php. Hackers target these files because they are often executed by WordPress. Hackers could also modify the header. php file in your WordPress installation using a coded string and PHP's eval () function.
3. installing a plugin or theme that modifies other files
Another common way for a malicious redirect to infect a site is to ask the website owner to unwittingly install an infected plugin or theme. The solution to this type of attack was to delete the plug-in and restore your website's old .htaccess.
4. infecting JavaScript files with malicious code
Another malicious redirect attack was identified in 2017. This attack injects malicious JavaScript code into every .js file available on your website.
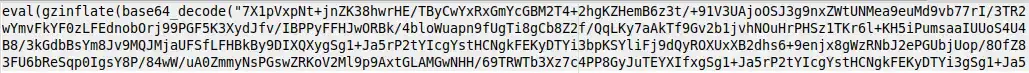
The malicious code can be recognised by the long hex-encoded strings it places in the files. These sections of code look something like:
Removing WordPress redirects is generally a simple process.
1- Change your passwords and check registered users
If a hacker manages to gain access to your administration section, you will need to change the passwords of all WordPress users. You will also need to ensure that no additional users have been added by the hacker. For added security, you should also generate new WordPress salt keys and passwords for FTP accounts, databases and hosting accounts.
2-Delete all unexpected plugins and themes from the site
The presence of unexpected themes or plugins may indicate that your site has been compromised. Delete all these files.
3- Scan your website with an appropriate tool
There are a number of tools that can scan your website for malware and infected files, such as: SUCURI
4- Use a WordPress plugin to scan your files
There are a variety of plug-ins that will scan your WordPress system files to ensure they are correct. These scanners will identify any malicious code added to files such as index.php, db.php, header.php and footer.php. The Security and Monitoring plugin, which can analyse and identify whether WordPress core files have been modified or infected.
5- Manually inspect vulnerable files
If the problem persists, you can manually inspect the files that often contain this type of attack. This includes your .htaccess files, your index.php and db.php files. This attack also appears in your theme's header.php and footer. php files. Look for long coded strings and javascript calls to remote websites.
6- Reinstall your WordPress files, plugins and themes
If the problem persists, restore an older backup of your website. If you do not have a backup of your website, carry out a complete reinstallation of all WordPress files, plug-ins and themes.
It's important to take steps to ensure this infection doesn't happen again. The following steps will significantly reduce the risk of another attack.
Change your passwords
Make your passwords more complex so that hackers are less likely to use a successful brute force attack on your website. Your passwords should also be changed regularly. Install
Installing WordPress security software
You can install security software such as All In One WP Security & Firewall
Install a plugin to check the integrity of Wordpress files
You can also install a plugin that checks the integrity of your files by comparing them with the files in the official Wordpress repository. This plugin can discover malicious code in your theme's Javascript, header.php, index.php and footer. php files.
Never install plugins or themes from untrusted sources
Whenever possible, get your plugins from the official WordPress site. Don't install plugins or themes unless you really need the functionality they offer. If you don't use a plugin or theme, delete it from your website.
Keep all themes and plugins updated
WordPress themes and plugins sometimes contain vulnerabilities that can be exploited by hackers . update to minimise the risk of vulnerability.
Make sure your WordPress installation is regularly backed up
It is essential to regularly back up your website in order to recover quickly from this type of attack.
You are now able to disinfect your WordPress site that redirects to other websites. Don't hesitate to share your comments and questions!
Rate this article :
5/5 | 2 opinion
This article was useful to you ?
Yes
No
2mn reading
How do I activate an https url on Wordpress?
3mn reading
How to secure your Wordpress site
0mn reading
How can you force HTTPS protocol on your Wordpress site?
2mn reading
How do I unblock a blocked IP on Wordpress?